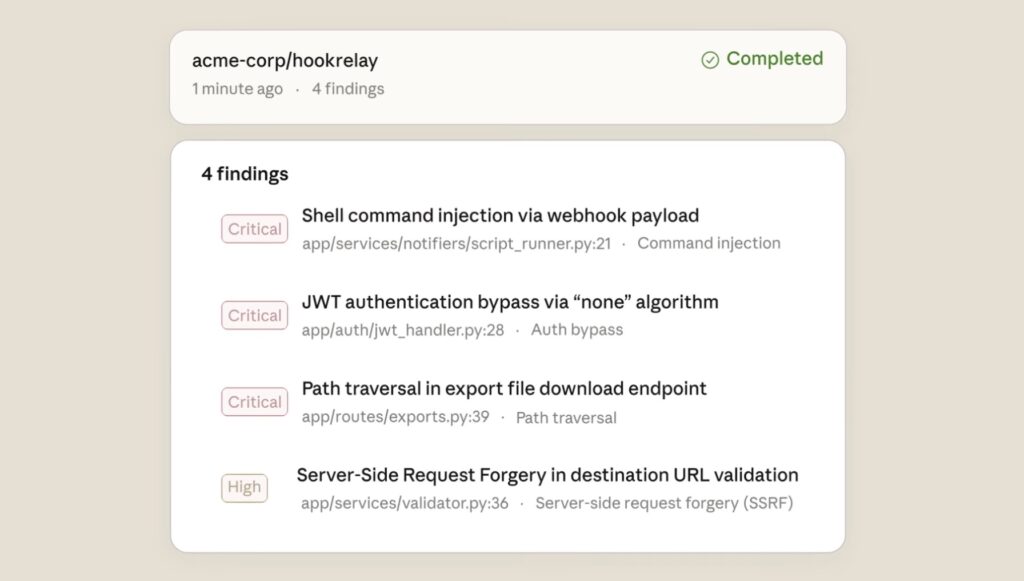
From Identifying Patterns to Understanding Intent—The New Frontier of AI-Driven Cybersecurity
- A Shift from Rules to Reason: Unlike traditional static analysis that relies on known patterns, Claude Code Security uses human-like reasoning to identify complex vulnerabilities in business logic and data flow.
- Human-Centric Control: The system employs a multi-stage verification process to filter false positives and provides suggested patches, but ensures developers remain the final decision-makers.
- Proactive Defense for the AI Era: By making frontier capabilities available to enterprise teams and open-source maintainers, the tool aims to find and fix “undiscoverable” bugs before attackers can exploit them.
The cybersecurity landscape has long been defined by a grueling war of attrition. Security teams are perpetually outnumbered, facing a tidal wave of software vulnerabilities with a limited pool of skilled researchers. While traditional automated tools have helped stem the tide, they generally act as “pattern matchers”—effective at spotting a reused password or an outdated encryption library, but blind to the subtle, context-dependent flaws that savvy attackers thrive upon.
To bridge this gap, Anthropic is introducing Claude Code Security, a new capability currently in a limited research preview. Built directly into the Claude Code web interface, this tool represents a fundamental shift in how we approach code safety. It doesn’t just scan for mistakes; it reasons through the codebase, understanding how disparate components interact and tracing the movement of sensitive data the way a seasoned security analyst would.
The Evolution of the Audit
The core innovation of Claude Code Security lies in its departure from standard “static analysis.” Most existing tools are rule-based, which makes them rigid. If a vulnerability doesn’t match a pre-defined signature, it goes undetected. Claude Code Security, however, addresses the “un-patchable” middle ground: flaws in business logic and broken access controls that require an understanding of the software’s intent.
To ensure that teams aren’t overwhelmed by “noise,” every finding undergoes a rigorous multi-stage verification process. Claude essentially plays devil’s advocate with itself, attempting to disprove its own findings to filter out false positives. When a vulnerability is confirmed, it is presented in a dedicated dashboard with a severity rating and a confidence score. Crucially, the tool suggests targeted software patches, allowing developers to review and approve fixes rather than starting from scratch.
Proven in the Trenches
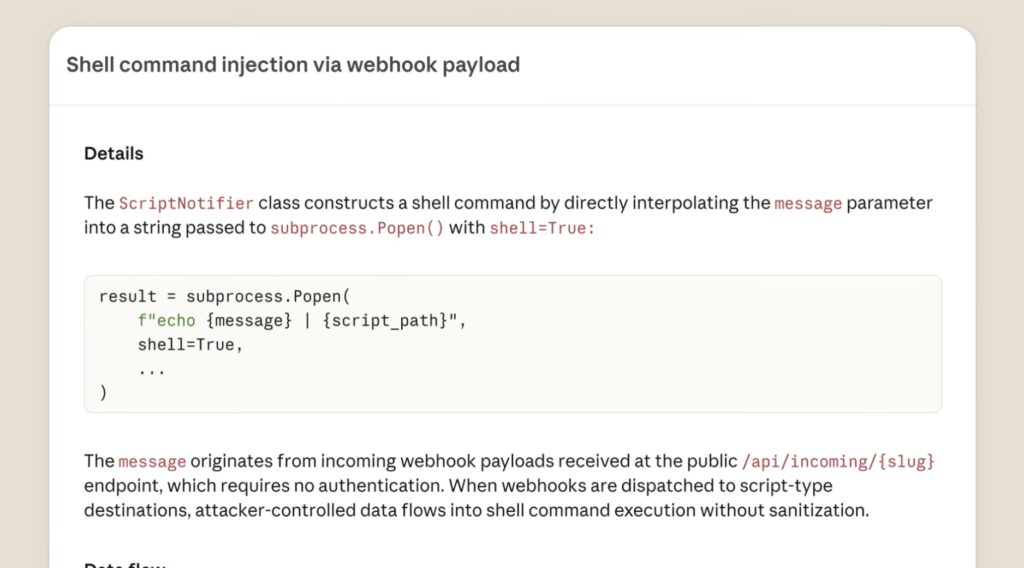
This isn’t just theoretical technology. Claude Code Security is the culmination of over a year of stress-testing by the Frontier Red Team. From competing in high-stakes “Capture-the-Flag” events to partnering with the Pacific Northwest National Laboratory to defend critical infrastructure, the model’s defensive muscles have been meticulously trained.
The results are striking. Using Claude Opus 4.6, researchers recently identified over 500 vulnerabilities in production open-source codebases—some of which had remained hidden for decades despite repeated expert audits. By using these same tools to secure Anthropic’s own internal systems, the team has proven that AI can significantly raise the security baseline of even the most sophisticated tech stacks.
Winning the AI Arms Race
We are entering a pivotal era where AI will inevitably be used by both sides of the cybersecurity divide. Attackers will leverage these models to find exploitable weaknesses at unprecedented speeds. Claude Code Security is designed to ensure that defenders move faster. By putting frontier-grade analysis into the hands of Enterprise users and providing expedited, free access to open-source maintainers, the goal is to patch the world’s code before it can be weaponized.
The road ahead suggests a future where the majority of the world’s code is scanned and hardened by AI. While the technology is powerful, the philosophy remains human-led: AI identifies the problems and suggests the solutions, but the human developer always makes the final call.

